Cloud SQL Auth Proxy
Part of Working with Cloud SQL
Tutorial
- Why do we need a tool like the Cloud SQL Proxy?
- What is the Cloud SQL Auth Proxy?
- How does the Cloud SQL Proxy solve these problems?
- How can you use the Cloud SQL Proxy?
- What’s next?
- References
Welcome to the third tutorial in the series: “Working with Cloud SQL.” In the previous tutorial, we looked more at how we can ensure that the MySQL command-line tools establish a secure connection to a Cloud SQL instance.
In this tutorial, we will look at a different approach for connecting: The Cloud SQL Auth Proxy.
Why do we need a tool like the Cloud SQL Proxy?
Connecting securely to a Cloud SQL instance through the MySQL command line is not ideal:
- You need to maintain all the certificates.
- You need to remember the IP address of your instance or set up a domain name.
- You need to allow access to the IP that you’re connecting from on the Cloud SQL instance.
- In most cases, it is not you who will be connecting but your applications.
The Cloud SQL Proxy solves most of these problems.
What is the Cloud SQL Auth Proxy?
The Cloud SQL Auth Proxy is an application that sits between your application and the Cloud SQL database instance. Rather than connecting directly to the Cloud SQL database, your application connects to the Cloud SQL Proxy, which opens a secure connection to the database for you.
How does the Cloud SQL Proxy solve these problems?
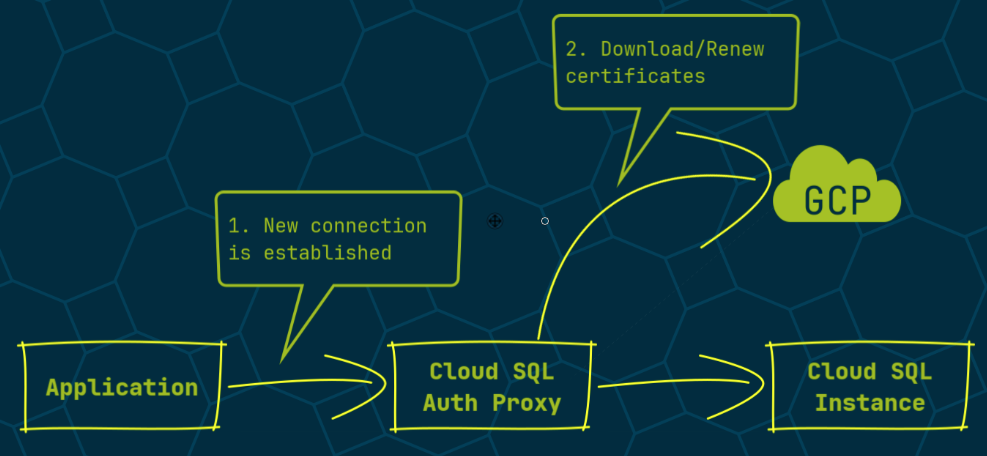
- When you open a new connection, the proxy automatically downloads and renews the local certificates.
- Instead of remembering the IP address of your instance, you use the more easy-to-remember “connection name,” which consists of the “project id,” “instance name,” and zone or region.
- Rather than verifying that traffic comes from the correct IP, the proxy uses a Google Cloud principal, a user or service account, to authenticate before opening a connection.
- Finally, you can use any application to connect through the proxy to your Cloud SQL instance as long as the application works with your standard database connection protocol.
How can you use the Cloud SQL Proxy?
Let’s walk through a real-life example.
I've already created a Cloud SQL instance and a Compute Engine instance with the MySQL command-line tools installed so that we can focus on the core aspect of the demo, the Cloud SQL Proxy. If you want to see how to configure these instances, check out the first tutorial in this series.
Let’s start an SSH session on the Compute Engine instance. My instance is called “cloud-sql-proxy-demo.”
gcloud compute ssh cloud-sql-proxy-demo --project <project-id>
The next step is to install the Cloud SQL Proxy. The instructions are in the Google Cloud documentation. I read through these instructions and provided the relevant commands below.
The first command is a curl command that downloads the Cloud SQL Proxy binary.
curl -o cloud-sql-proxy https://storage.googleapis.com/cloud-sql-connectors/cloud-sql-proxy/v2.3.0/cloud-sql-proxy.linux.amd64
Then we use chmod to make the binary executable.
chmod +x cloud-sql-proxy
That’s all there is to the installation of the proxy. If you want to have the proxy available permanently, don’t forget to turn it into a Linux system service.
Before we can connect to the Cloud SQL instance, we need to figure out the Cloud SQL instance connection name. We can use the Google Cloud command line to get this name.
gcloud sql instances describe cloud-sql-proxy-demo --project <project-id> --format 'value(connectionName)'
This should give an output like the one shown below:
<project-id>:europe-west1:cloud-sql-proxy-demo
We can then use the connection name to connect to our instance.
./cloud-sql-proxy <project-id>:europe-west1:cloud-sql-proxy-demo<connection-name>
And — that doesn’t work. The main reason for this failure is a permissions issue. For the Cloud SQL Proxy to renew certificates and open a connection to the instance, it needs to run with a Google Cloud service account that is allowed to connect to the Cloud SQL instance. Since we didn’t configure a service account at the Cloud SQL Proxy level, the Cloud SQL Proxy uses the Compute Engine instance’s service account.
Let’s open the Google Cloud Console to add the missing permission.
In the IAM page of the Google Cloud Console, we need to click on the “Grant access” button. Clicking this button opens a side panel where we can enter the principal’s name. I’ve created a “cloud-sql-proxy-demo” service account for this demo, which I’ve configured on the Compute Engine instance. All we need for connectivity to work is to grant this account the required access.
In the name field, enter the name of the service account that you’ve configured at the Compute Engine level. I will enter “cloud-sql-proxy-demo” here and select the actual service account shown in the autocomplete field. Once we’ve chosen a service account, we need to specify the role we want to grant to this account.
Three roles contain the permission to connect to an instance: Cloud SQL Admin, Cloud SQL Editor, and Cloud SQL Client. Because we don’t want to give our Compute Engine instance too many permissions, we will grant the Cloud SQL Client role, as this role has the least privileges. Click “Save” to grant the role.
Now that we’ve granted the required role, we can switch back to our terminal session.
In our terminal, we can execute the ./cloud-sql-proxy command again to try establishing a connection.
./cloud-sql-proxy <project-id>:europe-west1:cloud-sql-proxy-demo<connection-name>
The Cloud SQL Proxy now starts correctly.
Open a new SSH session to the Compute Engine instance in a second terminal window.
gcloud compute ssh cloud-sql-proxy-demo --project <project-id>
We will connect to the Cloud SQL Proxy from this second SSH session through the Cloud SQL Proxy. As explained earlier, the Cloud SQL Proxy encrypts the connection for us, so we can use a straightforward MySQL command to connect to the proxy running on this server. The proxy, in turn, will open a connection to the Cloud SQL instance.
mysql -h 127.0.0.1 -P 3306 -u root -p
That’s it. We successfully connected to our Cloud SQL instance. You can validate the encrypted connection using the MySQL status; command.
What’s next?
You’re ready to start using the Cloud SQL Proxy for your projects. Be aware that if you’re using Java, Python, or Go, there is a more straightforward approach for connecting to a Cloud SQL instance through programming-language-specific connectors. In the following tutorials, we will explore doing so in both Java and Python.